LLHOST
Member
LLHOST INC. is a European company established in 2017 by engineers of 10+ years of hosting, network and development industries experience. We provide a diverse spectrum of services, starting from Hosting services, as our main product, through the Internet Exchange and Network services to a System administration and Development teams outsourcing and outstaffing. We introduce our OVS (Optimized Virtual Servers) - a bunch of LLHOST INC. VPS plans based on KVM virtualization that could be used for most common tasks.
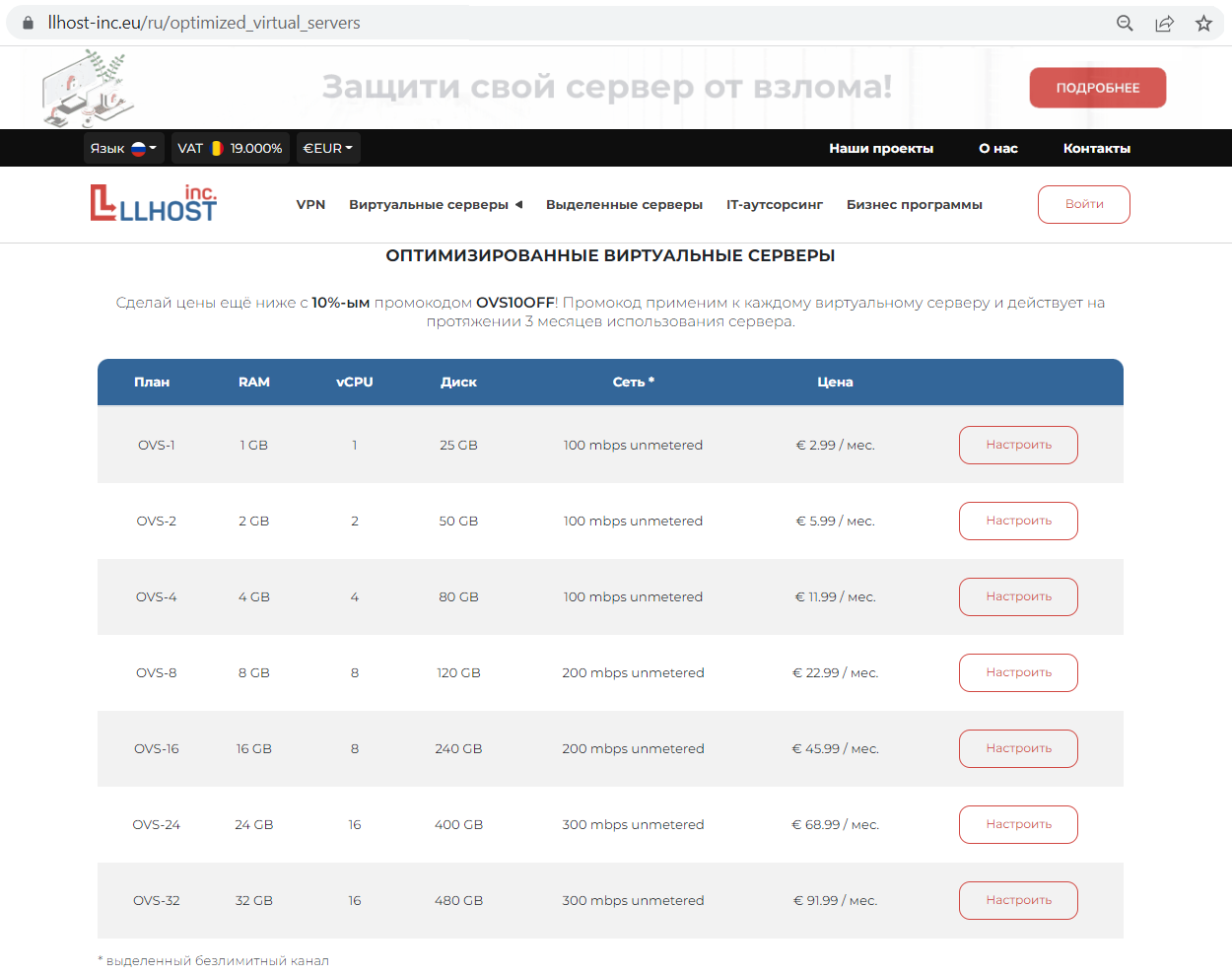
Each OVS plan includes:
OVS-1: 1GB RAM, 1 vCPU, 25GB SSD, 100 mbps unmetered - Configure
OVS-2: 2GB RAM, 2 vCPU, 50GB SSD, 100 mbps unmetered - Configure
OVS-4: 4GB RAM, 4 vCPU, 80GB SSD, 100 mbps unmetered - Configure
OVS-8: 8GB RAM, 8 vCPU, 120GB SSD, 200 mbps unmetered - Configure
OVS-16: 16GB RAM, 8 vCPU, 240GB SSD, 200 mbps unmetered - Configure
OVS-24: 24GB RAM, 16 vCPU, 400GB SSD, 300 mbps unmetered - Configure
OVS-32: 32GB RAM, 16 vCPU, 480GB SSD, 300 mbps unmetered - Configure
Make prices even lower with a Payment for 3 months - 15% discount
Payment for 6 months - 20% discount
Payment for 12 months - 25% discount
Our locations:
Our contacts:
E-mail: sales@llhost-inc.eu
Send a request: Sales Department
Facebook
LinkedIn
Each OVS plan includes:
- 100 mbps Internet channel to each VPS
- Unlimited bandwidth
- Free/64 IPv6 to each VPS
- Instant deployment
- User-friendly VPS control panel with embedded popular scripts and images
- Free migration assistance
- 24/7 prompt technical support (max response time: 5-10 min.)
OVS-1: 1GB RAM, 1 vCPU, 25GB SSD, 100 mbps unmetered - Configure
OVS-2: 2GB RAM, 2 vCPU, 50GB SSD, 100 mbps unmetered - Configure
OVS-4: 4GB RAM, 4 vCPU, 80GB SSD, 100 mbps unmetered - Configure
OVS-8: 8GB RAM, 8 vCPU, 120GB SSD, 200 mbps unmetered - Configure
OVS-16: 16GB RAM, 8 vCPU, 240GB SSD, 200 mbps unmetered - Configure
OVS-24: 24GB RAM, 16 vCPU, 400GB SSD, 300 mbps unmetered - Configure
OVS-32: 32GB RAM, 16 vCPU, 480GB SSD, 300 mbps unmetered - Configure
Make prices even lower with a Payment for 3 months - 15% discount
Payment for 6 months - 20% discount
Payment for 12 months - 25% discount
Our locations:
- Amsterdam (Netherlands):Katowice (Poland): 4 Data Center, (Adamskiego 7, Katowice, PL, 40-069).
- Fremont (USA): Hurricane Electric Fremont 2 (48233 Warm Springs Blvd, Fremont, CA, USA, 94539).
- Custom configurations: in addition to basic plans, we are ready to provide our clients with custom solutions and configurations upon request.
- Prompt technical support 24/7/365: Maximum response time to tickets is 10 minutes. Technical support is provided in English and Russian languages.
- Fixed prices and prepayments: We work exclusively on prepayment basis and do not charge additional charges for excessed traffic, volumes, speed, etc.
- Individual approach: we are always happy to discuss individual conditions (discounts, terms, partnerships, etc.) with our clients - open the ticket and our managers will be happy to help you.
- Transparency: Our customers always know how much and for what they pay. No additional payments in small print.
Our contacts:
E-mail: sales@llhost-inc.eu
Send a request: Sales Department